Process Library Services
Process Optimisation
Process Optimisation is a critical aspect of our Information Security consultation services. We recognise that effective information security relies on well-defined and optimised processes that align with industry best practices and regulatory standards. Through our comprehensive Process Optimisation offerings, we help businesses with streamlining their security operations, enhance efficiency, and ensure compliance. Our experienced consultants work closely with clients to identify areas for improvement, map out existing processes, and implement tailored solutions that address specific business challenges. Whether you're struggling with continuous improvement, quality control, governance, technology alignment, or regulatory compliance, our Process Optimisation services provide the expertise and guidance needed to transform your information security processes into a competitive advantage.
The Noun-Verb Method for Process Modelling
The Noun-Verb method is a widely used technique for creating clear and consistent process models. It helps to standardise the way processes are documented, making them easier to understand and follow. The method revolves around using specific shapes to represent different elements of a process, with each shape labeled according to its purpose.
- Ovals or Circles: Used to represent the start and end points of a process, labeled with a noun (e.g., "Incident Response Process").
- Rectangles: Used to represent activities or steps in the process, labeled with a verb (e.g., "Identify Incident").
- Rounded Corner Rectangles: Used to represent deliverables or outputs produced by activities, labeled with a noun (e.g., "Incident Report").
- Diamonds: Used to represent decision points in the process, labeled with a question or condition (e.g., "Requires external assistance?").
- Arrows: Used to connect the shapes in the order of the process flow, indicating the logical sequence and decision paths.
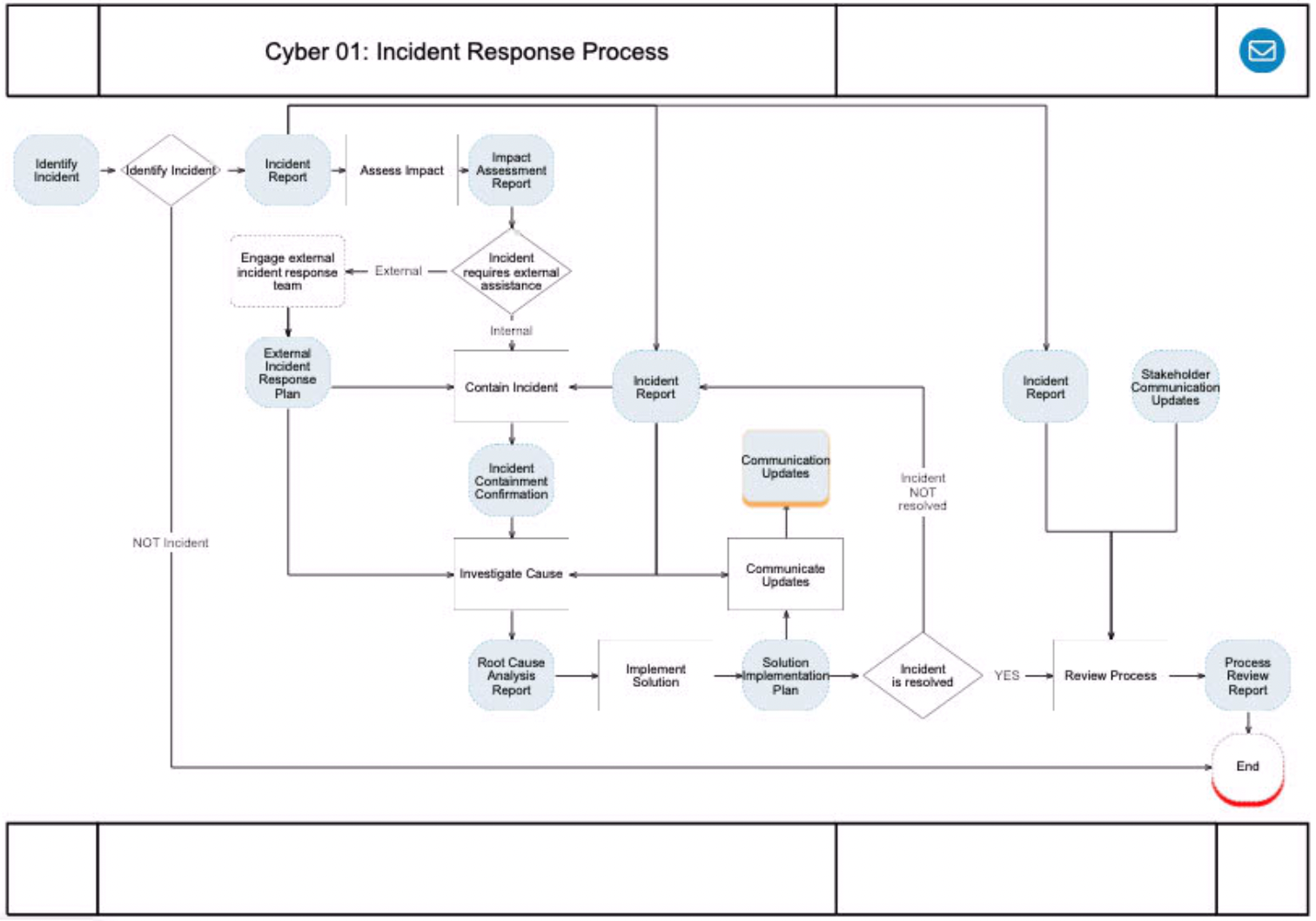
By following the Noun-Verb method, organisations can create standardised and easily understandable process models, fostering consistency and clarity in their process documentation.
The Benefits of a Process Library for Cybersecurity
Implementing formal processes is crucial for effective cybersecurity management within an organisation. A process library provides a centralised repository of pre-defined and well-documented processes, offering numerous benefits:
-
Improved Consistency and Standardisation: A process library ensures that cybersecurity processes are consistently applied across the organisation, reducing variations and promoting best practices.
-
Enhanced Efficiency and Productivity: Well-defined processes streamline operations, minimise redundancies, and optimise resource allocation, leading to increased efficiency and productivity.
-
Compliance and Regulatory Adherence: Many cybersecurity regulations and standards mandate the implementation of specific processes. A process library can help organisations meet these requirements and demonstrate compliance.
-
Knowledge Sharing and Training: A process library serves as a valuable knowledge base, facilitating the training of new employees and enabling knowledge transfer across teams.
-
Risk Mitigation and Incident Response: Clearly documented processes for risk assessment, incident response, and other critical cybersecurity functions can help organisations proactively identify and mitigate potential threats.
-
Continuous Improvement: By reviewing and updating processes in the library, organisations can identify areas for improvement and implement necessary changes, fostering a culture of continuous improvement.
Get Started with our Free Process Library Offer
Businesses come in all shapes and sizes. To help you get started, we offer a free process library tailored to meet the general cybersecurity needs of many different organisations. Our gratis library includes pre-defined processes for:
- Security policy development and enforcement
- Data encryption and protection
- Security monitoring and detection
- Identity and access management
- Risk assessment and management
- Security awareness training
- Access control management
- Patch management
- Vulnerability management
- Incident response
All these processes are designed using the Noun-Verb method, ensuring clarity and consistency in their documentation.
Get Free Access to Our Process Library
We believe in empowering organisations with the tools and knowledge necessary to strengthen their cybersecurity posture. That's why we offer free access to our process library for anyone who signs up for our SaaS-based subscription.
By subscribing, you'll gain access to our comprehensive collection of pre-defined processes, along with regular updates and enhancements. Our user-friendly platform allows you to explore, customise, and implement these processes within your organisation, ensuring a streamlined and standardised approach to cybersecurity management.
Bespoke Solutions for Your Unique Needs
While our process library covers a wide range of cybersecurity processes, we understand that every organisation has unique requirements. That's why we offer personalised consultations to help you build a tailored solution that aligns with your specific needs and objectives.
Our team of cybersecurity experts will work closely with you to assess your current processes, identify gaps, and develop a customised plan to enhance your cybersecurity posture. We'll leverage our extensive experience and industry best practices to ensure that your organisation is equipped with the right processes and tools to safeguard your digital assets and mitigate potential risks effectively.
Whether you're looking to implement a comprehensive cybersecurity program or optimise specific processes, our bespoke solutions will provide you with the guidance and support you need to achieve your goals.
Get Started Today
Unlock the power of standardised and well-documented cybersecurity processes by subscribing to our process library. Enhance your organisation's security posture, streamline operations, and stay ahead of evolving threats with our comprehensive offerings.
Contact us today to learn more about our process library, schedule a consultation, or explore our bespoke solution offerings. Together, we'll build a stronger and more resilient cybersecurity foundation for your organisation.
Speak To Us